Getting Started
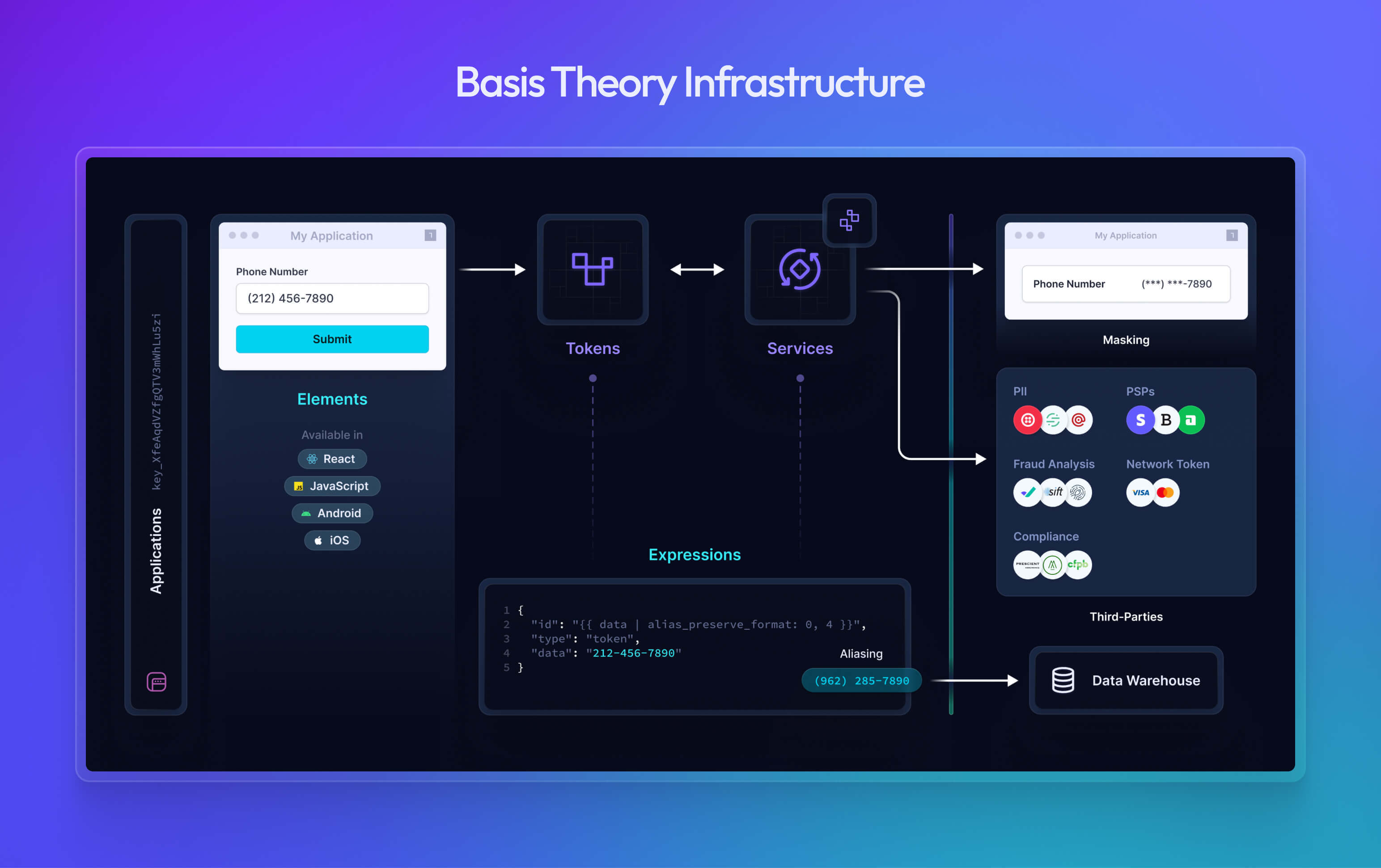
Basis Theory provides APIs, SDKs, and all of the tools you need to make your sensitive data more secure and usable.

What is Basis Theory?
Our software becomes a core part of your infrastructure enabling you to quickly encrypt, tokenize, and store any payload securely. Your token infrastructure can be used to protect data at rest, as it passes between your own internal systems, or how it's permissioned and shared with third parties.
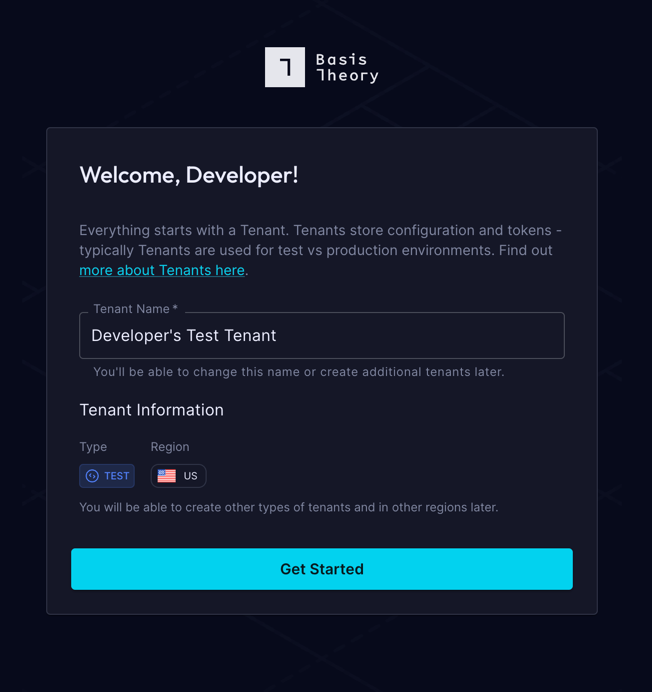
1. Set up your Test Account
Head over to the Basis Theory Portal and create a Personal Account using your work email (e.g., john.doe@yourcompany.com)
In the Portal's Welcome Page, create a TEST Tenant - the place where your tokens and other resources are stored:
2. Start Building
Jump into action with a step-by-step guide tailored to your use case.
Collect Cards
Issue Cards
Receive Cards via API / Webhooks
Collect Inbound Sensitive Data
Explore the Guides menu for more developer-centric guides or click the Ask AI ✨ button in the bottom right corner of this page.
3. Go Live
Visit our interactive checklist to ensure you are following the best recommended practices and go live without overthinking it.
Try a Blueprint
Blueprints are end-to-end guides around common use cases with the Basis Theory platform to help reduce or eliminate the compliance, regulatory, and security burdens.
Cards Blueprints
Personal Information Blueprints
Learn More
Access Controls
Tokens
Expressions
Proxy
Reactors
Search