What Is the Proxy?
It is a common need to share data between software systems via HTTP based APIs. But what if an outbound HTTP request from your system requires a piece of sensitive data that you have tokenized and do not want to access directly within your application? Or what if your API receives inbound HTTP requests that contain sensitive data that you wish to tokenize before it hits your servers?
The Proxy allows you to use tokens with HTTP APIs without needing to access sensitive data directly within your systems. This enables solving both these problems securely while keeping your systems out of compliance scope.
There are two options available when proxying HTTP requests
-
- How it works: Call the proxy API with all settings (destination, tokens, etc.) in the request. No prior setup needed.
- Use case: Basic tasks, like sending tokenized data to a third-party API, without additional customization.
-
- How it works: Create a proxy instance with a unique key and set configuration upfront, then use it as needed.
- Use case: Scenarios requiring fixed settings, such as whitelisting destinations in production, or cases where custom logic might be added.
- Optional feature: Request/response transforms with custom code.
Outbound Requests
Outbound HTTP requests initiated from your system can include tokens within the request payload, and the proxy can detokenize and substitute the token data into the request before forwarding it to the desired destination. This makes it easy to share sensitive data with a third party without needing to first retrieve and manipulate this sensitive data on your servers.
How It Works
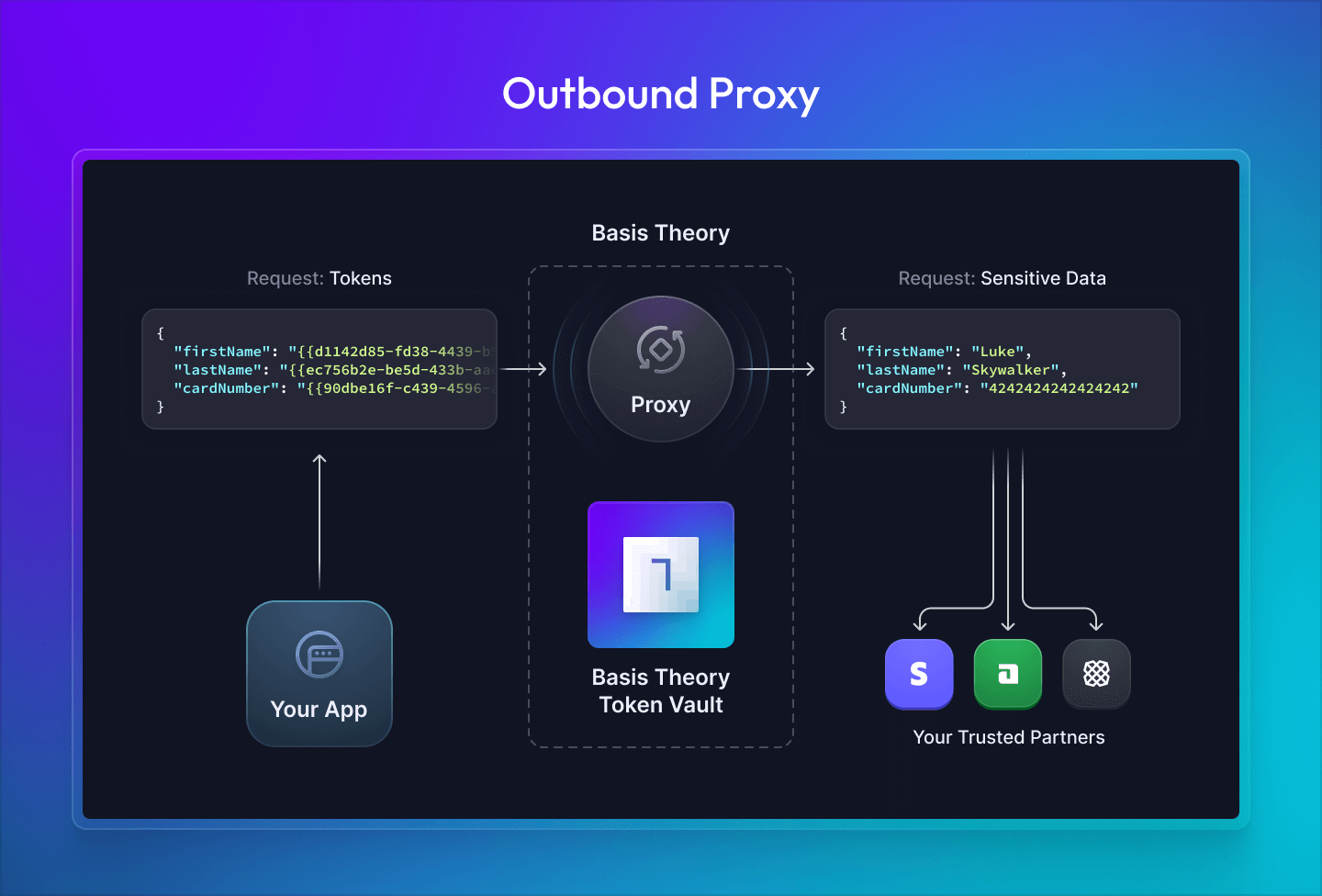
Your system initiates an outbound HTTP request to the Ephemeral Proxy or a Pre-Configured Proxy instance hosted by Basis Theory.
To include sensitive data in your request, you include token identifiers within expressions included in the request.
These are patterns of the form {{<tokenId>}}, where <tokenId> is the id of a token created within your Basis Theory tenant.
The request is transformed by evaluating each expression and substituting the resulting plaintext values within the request.
Finally, the transformed request containing sensitive data is delivered to the configured destination URL.
The Proxy terminates the inbound TLS connection from your servers and initiates a new TLS connection to the destination in order to guarantee secure transmission of your sensitive token data.
Whatever the content type or HTTP method, any HTTP request can be sent through the Proxy. For further details, check out our API docs.
Examples
- Stripe
- Adyen
- Chase (Orbital)
- Chase (Stratus)
- Braintree
- TabaPay
- Authorize.net
- Checkout.com
- NMI
- Paysafe
- Nuvei
- Finix
- dLocal
- FlexFactor
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://api.stripe.com/v1/payment_methods' \
-H 'Authorization: Bearer sk_test_51KMGNYGuvJF9SIWEW0y4rKcaQwLVLck2rGB8UEPHzSp1utx7gXKAfZ3DVgjMfAuvBIT42pQhg0sIx2PepEJkXv9g00yIrUwhI4' \
-H 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'type=card' \
--data-urlencode 'card[number]={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.number" }}' \
--data-urlencode 'card[exp_month]={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data" | card_exp: "MM" }}' \
--data-urlencode 'card[exp_year]={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data" | card_exp: "YYYY" }}' \
--data-urlencode 'card[cvc]={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.cvc" }}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://checkout-test.adyen.com/v69/payments' \
-H 'X-API-KEY: Vt(JJ5U5xuVECtg59fm9hBM+cZMWhw+ms2edxM%Rwmu0=Z2n3rGiQjQr-YEYfAq((It-Ocb03Jfob1JqGhogg:J/skGLIwerM=uAuHQDFHZBh+75pKgznYB3QeL7mrnBSeh34YAxLjdGEJQAhKdaU2' \
-H 'Content-Type: application/json' \
-d '{
"amount": {
"value": 100,
"currency": "USD"
},
"paymentMethod": {
"type": "scheme",
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expiryMonth": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"expiryYear": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}",
"cvc": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}",
"holderName": "John Smith"
},
"reference": "YOUR_ORDER_NUMBER",
"shopperInteraction": "Ecommerce",
"recurringProcessingModel": "CardOnFile",
"storePaymentMethod": "true",
"merchantAccount": "BasisTheoryECOM",
"shopperReference": "YOUR_UNIQUE_SHOPPER_ID",
"returnUrl": "https://your-company.com/..."
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://orbitalvar1.chasepaymentech.com/profile' \
-H 'orbitalConnectionUsername: TESTMYCOMPANY1234' \
-H 'orbitalConnectionPassword: f1nwbj32VwW36tV16s55' \
-H 'merchantID: MERCHANTID1234' \
-H 'Content-Type: application/json' \
-d '{
"version": "4.3",
"merchant": {
"bin": "000001"
},
"order": {
"customerProfileFromOrderInd": "A",
"customerProfileOrderOverideInd": "NO"
},
"paymentInstrument": {
"customerAccountType": "CC",
"card": {
"ccAccountNum": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"ccExp": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYYMM\" }}"
}
},
"profile": {
"customerName": "John Smith",
"customerAddress1": "123 Main St",
"customerCity": "Tampa",
"customerState": "FL",
"customerZIP": "33601"
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://netconnectvar1.chasepaymentech.com/NetConnect/controller' \
-H 'Auth-MID: M987654321012345' \
-H 'Auth-User: TESTMYCOMPANY1234' \
-H 'Auth-Password: f1nwbj32VwW36tV16s55' \
-H 'Stateless-Transaction: true' \
-H 'Content-Type: SALEM05210/SLM' \
-d 'P74VPMT-18R86WXMM9
VI{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.number" | pad_right: 19, "x" }}{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data" | card_exp: "MMYYYY" }}00003319380000000000008407202NVF AB
XX XXX XXXXX XXXXXXX XX
USABBEVILLE LA70510-7288AC01YEI10000000014064
7930f35b3c06cffe FR1XXXXMTCSTO
000000000000'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://payments.sandbox.braintree-api.com/graphql' \
-H 'Authorization: Basic 123' \
-H 'Braintree-Version: 2019-01-01' \
-H 'Content-Type: application/json' \
-d '{
"query": "mutation TokenizeCreditCard($input: TokenizeCreditCardInput!){
tokenizeCreditCard(input: $input){
paymentMethod{
id
legacyId
usage
details{
... on CreditCardDetails{
brandCode
last4
expirationMonth
expirationYear
}
}
}
}
}",
"variables": {
"input": {
"creditCard": {
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\"}}",
"expirationMonth": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\"}}",
"expirationYear": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\"}}",
"cvv": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\"}}"
}
}
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://api.tabapay.net/v1/clients/MyClientID/accounts' \
-H 'Authorization: Bearer 123' \
-H 'Content-Type: application/json' \
-d '{
"card": {
"accountNumber": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expirationDate": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYYMM\" }}",
"securityCode": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}"
},
"owner": {
"name": {
"first": "John",
"last": "Smith"
},
"address": {
"line1": "123 Main St",
"city": "Tampa",
"state": "FL",
"zipcode": "33601"
}
},
"referenceID": "reference_123"
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://apitest.authorize.net/xml/v1/request.api' \
-H 'Content-Type: application/json' \
-d '{
"createTransactionRequest": {
"merchantAuthentication": {
"name": "K5yH8dL2zGx",
"transactionKey": "J7rXuPbNvQ9sE3wA"
},
"refId": "123156121",
"transactionRequest": {
"transactionType": "authCaptureTransaction",
"amount": "25",
"payment": {
"creditCard": {
"cardNumber": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expirationDate": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY-MM\" }}",
"cardCode": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}"
}
}
}
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://api.sandbox.checkout.com/payments' \
-H 'Authorization: Bearer sk_sbox_p4qr9st2uy7vx1wa3bc8dl5zg6x'
-H 'Content-Type: application/json' \
-d '{
"source": {
"type": "card",
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expiry_month": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"expiry_year": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}"
},
"amount": 6500,
"currency": "USD",
"processing_channel_id": "processing_channel_id",
"reference": "ORD-5023-4E89",
"metadata": {
"udf1": "TEST123",
"coupon_code": "NY2018",
"partner_id": 123989
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://secure.safewebservices.com/api/transact.php' \
-H 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'type=sale' \
--data-urlencode 'amount=100.00' \
--data-urlencode 'orderid=5a4ab2409af89' \
--data-urlencode 'security_key=P4qR9sT2uY7vX1wA3bC8dL5zG6xK9yH2' \
--data-urlencode 'ccnumber={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.number" }}' \
--data-urlencode 'ccexp={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: "MMYY" }}' \
--data-urlencode 'cvv={{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.cvc" }}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://api.test.paysafe.com/paymenthub/v1/paymenthandles' \
-H 'Authorization: Basic 123'
-H 'Content-Type: application/json' \
-d '{
"merchantRefNum": "a9b2b8d2b9458c8beeb89dbce669",
"transactionType": "ORIGINAL_CREDIT",
"accountId": "1009688230",
"card": {
"cardNum": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"cardExpiry": {
"month": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" | to_number }}",
"year": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" | to_number }}"
},
"cvv": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}",
"holderName": "Dilip",
"issuingCountry": "US"
},
"paymentType": "CARD",
"amount": 100,
"currencyCode": "USD",
"customerIp": "172.0.0.1",
"billingDetails": {
"nickName": "Home",
"street": "TEST",
"city": "CA",
"state": "CA",
"country": "US",
"zip": "12345"
},
"merchantDescriptor": {
"dynamicDescriptor": "OnlineStore",
"phone": "1234567899"
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://ppp-test.nuvei.com/ppp/api/v1/payment.do' \
-H 'Content-Type: application/json' \
-d '{
"sessionToken": "3993eb0c-5f64-4a6c-b16c-485818eb76eb",
"merchantId": "427583496191624621",
"merchantSiteId": "142033",
"clientRequestId": "1C6CT7V1L",
"amount": "100",
"currency": "USD",
"userTokenId": "230811147",
"clientUniqueId": "12345",
"paymentOption": {
"card": {
"cardNumber": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expirationMonth": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"expirationYear": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}",
"CVV": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}",
"cardHolderName": "John Smith"
}
},
"deviceDetails": {
"ipAddress": "192.168.2.38"
},
"billingAddress": {
"firstName": "John",
"lastName": "Smith",
"email": "john.smith@email.com",
"country": "US"
},
"timeStamp": "20241105081132",
"checksum": "5582d0189dd440f4bbf960569ec22e77"
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://finix.sandbox-payments-api.com/payment_instruments' \
-u 'USsRhsHYZGBPnQw8CByJyEQW:8a14c2f9-d94b-4c72-8f5c-a62908e5b30e'
-H 'Content-Type: application/json' \
-d '{
"address": {
"city": "San Francisco",
"country": "USA",
"line1": "900 Metro Center Blv",
"postal_code": "94404",
"region": "CA"
},
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"security_code": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}",
"expiration_month": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" | to_number }}",
"expiration_year": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" | to_number }}",
"identity": "IDgWxBhfGYLLdkhxx2ddYf9K",
"name": "John Smith",
"type": "PAYMENT_CARD"
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://sandbox.dlocal.com/secure_cards' \
-H 'X-Date: 2024-11-15T10:00:47.172Z' \
-H 'X-Login: <DLOCAL_X_LOGIN>' \
-H 'X-Trans-Key: <DLOCAL_TRANS_KEY>' \
-H 'V2-HMAC-SHA256, Signature: {{ proxy | json: "$.request.headers.X-Login" | append: proxy.request.headers.X-Date | append: proxy.request.body | hmac: "sha-256", "<DLOCAL_SECRET>" | to_base16 }}' \
-H 'Content-Type: application/json' \
-d '{
"card": {
"holder_name": "John Doe",
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expiration_month": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4| json: \"$.data.expiration_month\" }}",
"expiration_year": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.expiration_year\" }}",
"cvv": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}"
},
"country": "US",
"payer": {
"document": "1234567890",
"email": "john.doe@email.com",
"name": "John Doe"
}
}'
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <API_KEY>' \
-H 'BT-PROXY-URL: https://api-sandbox.flex-charge.com/v1/tokenize?mid=1234567890&environment=abcdefgh0123456789' \
-H 'Content-Type: application/json' \
-d '{
"payment_method": {
"email": "johnwick@email.com",
"credit_card": {
"first_name": "Joe",
"last_name": "Jones",
"number": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"month": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"year": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}",
"verification_value": "{{ token: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}"
}
}
}'
Guides
Find use case-driven examples in our implementation guides:
Inbound Requests
Third parties that integrate into your systems by calling an HTTP API may include sensitive data within their requests. Inbound HTTP requests into your system can be routed through the proxy to parse and tokenize sensitive pieces of data and substitute non-sensitive token identifiers into the request payload before it reaches your servers.
How It Works
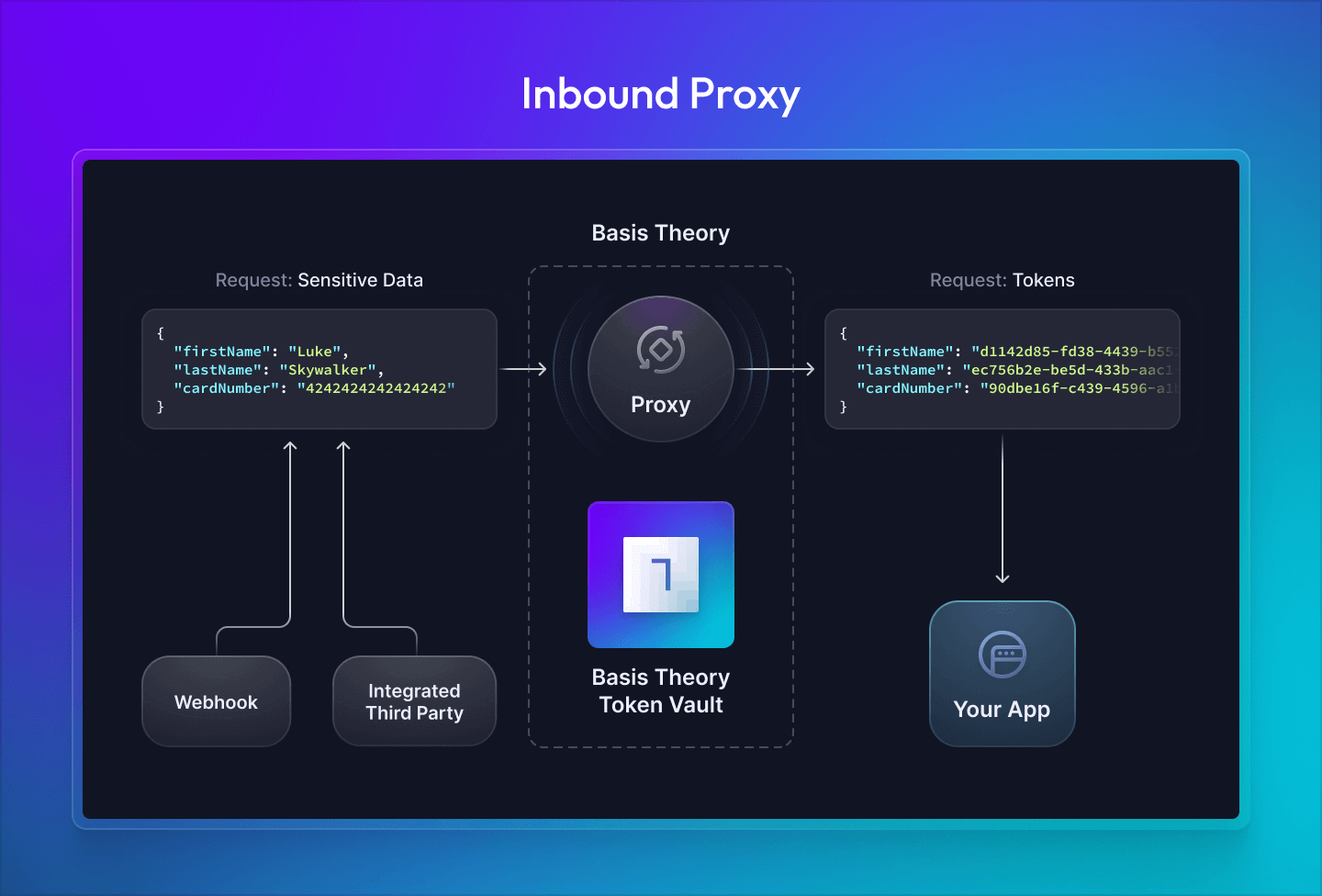
You pre-configure a proxy instance, which provides you a unique URL to this proxy that can be shared with a third party integrator. The third party can then make HTTP requests to this URL that pass through the proxy before being forwarded on to your system.
The proxy instance is configured with a request transform containing custom Node.js code that will execute within the proxy before the request is forwarded to your servers. This allows you to parse the request and tokenize sensitive data fields within the payload, substituting in non-sensitive tokens into the request. Your systems will receive a request containing the non-sensitive token identifiers that can be safely stored in your system.
Use a Custom Hostname for your Inbound Proxy
You can use a custom hostname in front of your Inbound Proxy to brand it as your own. This allows you to have clients and partners call an API like https://secure.yourdomain.com instead of the default proxy domain https://api.basistheory.com/proxy?bt-proxy-key=....
All you need to do is the following:
- Own a domain with a valid SSL certificate
- Create a new Pre-Configured Proxy instance
- Create a CNAME record pointing your custom hostname to
api.btproxy.cloud - Navigate to the Basis Theory Portal, find your Proxy and enter its details page. Click the "Request Custom Hostname" button, fill in the necessary information, and submit the request
- Basis Theory support will inform you of the TXT record(s) to create to validate domain ownership
Guides
FAQs
How to Choose Between the Proxy and Serverless Reactors
Basis Theory offers a number of out-of-the-box integrations to share your tokenized data with Third Party systems via our Serverless Reactor platform.
However, you may require an integration that is not yet supported, in which case you have a few options to choose from:
- Create a custom Reactor containing the code required to integrate with the third party system (our serverless platform executes this code)
- Use the Proxy to send the API request from your own application (your servers execute this code)
Using the Proxy can provide a quicker and lower configuration option for making custom HTTP requests to a third party API than writing and maintaining a Reactor.