Verify a Card
Streamline card verification with a secure, proxy-powered solution.Verifying a card is the process of confirming that the card details provided are valid and can be used for transactions. This operation, also known as card authentication, pre-authorization, or $0 authorization, typically involves sending a request to the card networks and issuers to validate the card's number, expiration date, and status. It ensures the card has not been reported lost or stolen and, in some cases, checks the availability of funds or credit.
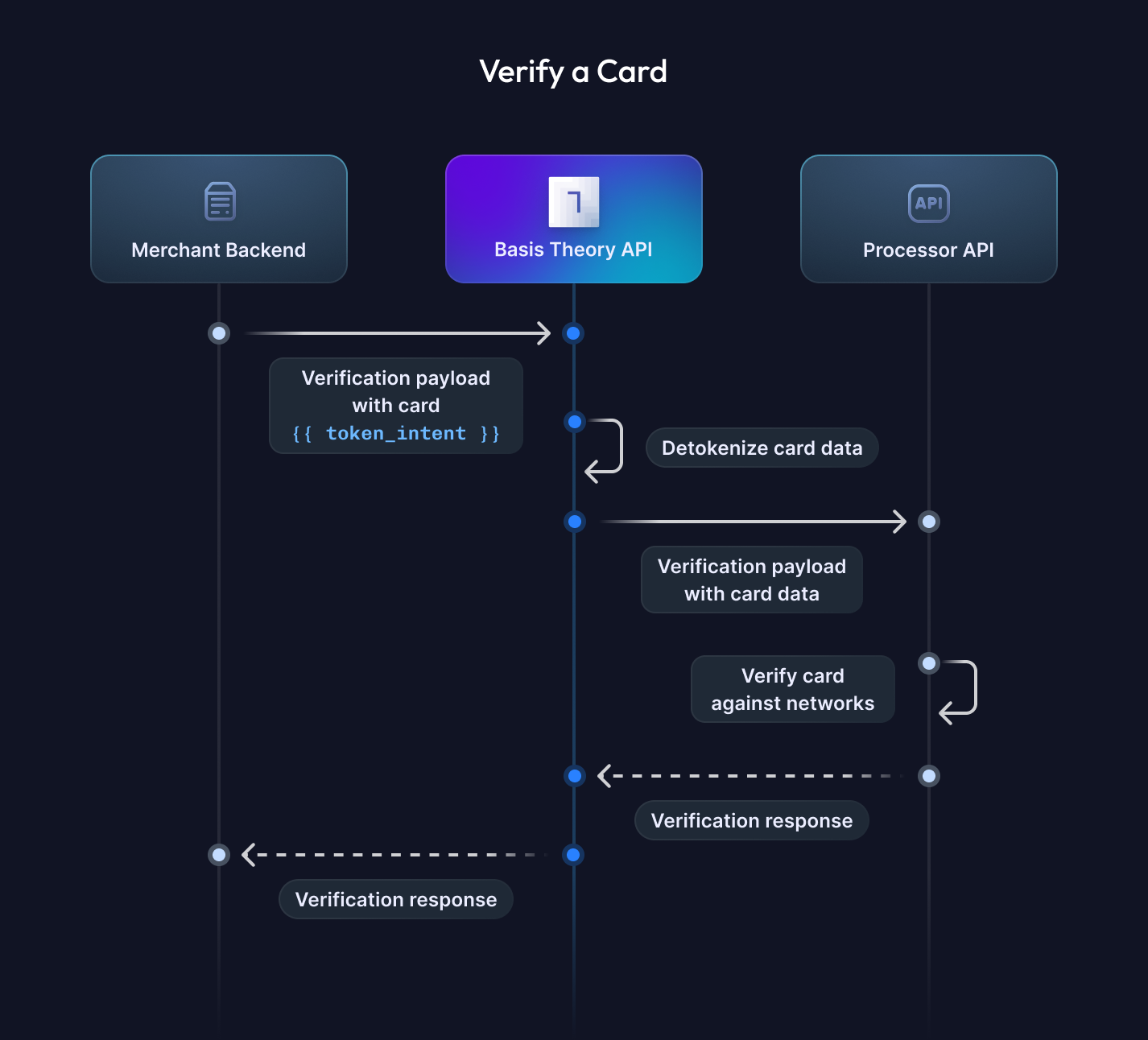
This guide will show you how to use the Proxy to verify a card with your chosen Payment Service Provider (PSP) while offloading PCI compliance scope with ease. We’ll explore a variety of processor-specific standards and their unique verification quirks, offering practical examples you can adapt to your selected PSP.
If you are not yet collecting your customers' cards with Basis Theory, here are a few guides you can explore:
- Replace Processor iFrames - capture cards in the frontend;
- Receive Cards via API / Webhooks - receive cards in API requests;
Getting Started
To get started, you will need to create a Basis Theory Account and a TEST Tenant.
Private Application
You will need a Private Application to allow your backend to call Basis Theory APIs. Click here to create one using the Basis Theory Customer Portal.
This will create an application with the following Access Controls:
- Permissions:
token:use,token:create
key from the created Private Application as it will be used later in this guide.Verify a Card
Different payment service providers (PSPs) may use varying workflows or terminology for this operation ($0 auth or ZDA, account verification, card validation, card ping, etc.). Regardless of the approach, card verification can enhance security, reduces fraud risks, and improves the reliability of payment processing.
Given you have previously created a Token Intent:
{
"id": "d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4",
"type": "card",
"tenant_id": "4aee08b9-5557-474b-a120-252e01fc7b0f",
"fingerprint": "BKJYqf2tcvhTHSXN7EvBJLviN3PBYRgwoJgce8VAfnSr",
"card": {
"bin": "424242",
"last4": "4242",
"expiration_month": 10,
"expiration_year": 2028,
"brand": "visa",
"funding": "credit",
"authentication": "sca_required",
"issuer_country": {
"alpha2": "GB",
"name": "UNITED KINGDOM OF GREAT BRITAIN AND NORTHERN IRELAND",
"numeric": "826"
}
},
"created_by": "0bc89db5-fadd-4d57-af93-10472e35ebd3",
"created_at": "2025-03-10T14:23:56.5580574+00:00",
"expires_at": "2025-03-11T14:23:56.5580575+00:00"
}
Here is how you can leverage the Ephemeral Proxy, a tool that transparently performs detokenization, to share the sensitive cardholder data to the Payments Processor or Acquirer API.
- Checkout.com
- Stripe
- Adyen
In Checkout.com, you can verify a card without charging it by calling the /payments API.
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <PRIVATE_API_KEY>' \
-H 'BT-PROXY-URL: https://api.sandbox.checkout.com/payments' \
-H 'Authorization: Bearer <CHECKOUT_SECRET_KEY>' \
-H 'Content-Type: application/json' \
--data '{
"source": {
"type": "card",
"number": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expiry_month": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"expiry_year": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}",
"cvv": "{{ token_intent: d96b9925-85d7-495e-88fe-a9c3ecb23b61 | json: \"$.data.cvc\" }}",
"store_for_future_use": true
},
"currency": "USD",
"processing_channel_id": "pc_svyx12xvaaduraq3ckb2gwnvzq"
}'
{
"id": "pay_myvj6zxrt45edgrswrliyxbtnq",
"approved": true,
"status": "Card Verified",
"source": {
"type": "card",
"id": "src_gguer4xlawke3ctljczft7573a",
"avs_check": "G",
"cvv_check": "Y",
...
},
"scheme_id": "647537243670773",
...
}
In Stripe, you can verify a card without charging it by saving the card to a customer.
- Create a Customer
- Create a Setup Intent using the Proxy
- This will create a new Payment Method (Processor Token), whose ID will be included in the response at
payment_method - If the card is invalid, this request may fail immediately.
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <PRIVATE_API_KEY>' \
-H 'BT-PROXY-URL: https://api.stripe.com/v1/setup_intents' \
-H 'Authorization: Bearer <STRIPE_SECRET_KEY>' \
-H 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'customer=cus_RTEOvM5dSx9RCS' \
--data-urlencode 'confirm=true' \
--data-urlencode 'payment_method_data[type]=card' \
--data-urlencode 'payment_method_data[card][number]={{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.number" }}' \
--data-urlencode 'payment_method_data[card][exp_month]={{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data" | card_exp: "MM" }}' \
--data-urlencode 'payment_method_data[card][exp_year]={{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data" | card_exp: "YYYY" }}' \
--data-urlencode 'payment_method_data[card][cvc]={{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: "$.data.cvc" }}'
{
"id": "seti_1QaI1YG9VRQ2700SF1DSos0x",
"status": "succeeded",
"object": "setup_intent",
"payment_method": "pm_1QaKJmG9VRQ2700S5JcsJv4Q",
"latest_attempt": {
"payment_method_details": {
"card": {
"network_transaction_id": "8723dfab9c4e56a1b8cd0291ef67ac43"
...
}
...
}
...
}
...
}
- Retrieve the Payment Method to get granular
checksinformation.
{
"id": "pm_1QaKJmG9VRQ2700S5JcsJv4Q",
"type": "card",
"object": "payment_method",
"card": {
"checks": {
"address_line1_check": "pass",
"address_postal_code_check": "pass",
"cvc_check": "pass"
}
...
}
...
}
In Ayden, you can verify a card without charging it by calling the /payments API with 0 value amount.
curl 'https://api.basistheory.com/proxy' \
-X 'POST' \
-H 'BT-API-KEY: <PRIVATE_API_KEY>' \
-H 'BT-PROXY-URL: https://checkout-test.adyen.com/v71/payments' \
-H 'X-API-Key: <AYDEN_API_KEY>' \
-H 'Content-Type: application/json' \
--data '{
"amount": {
"value": 0,
"currency": "USD"
},
"paymentMethod": {
"type": "scheme",
"number": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.number\" }}",
"expiryMonth": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"MM\" }}",
"expiryYear": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data\" | card_exp: \"YYYY\" }}",
"cvc": "{{ token_intent: d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4 | json: \"$.data.cvc\" }}",
},
"reference": "YourTransactionReference",
"shopperReference":"YourShopperId",
"shopperInteraction": "Ecommerce",
"recurringProcessingModel": "CardOnFile",
"storePaymentMethod": true,
"merchantAccount": "YourMerchantAccount"
}'
{
"pspReference": "HFGFCL72V3XW24V5",
"merchantReference": "YourTransactionReference",
"resultCode": "Authorised",
"amount": {
"currency": "USD",
"value": 0
},
"additionalData": {
"networkTxReference": "377216678422238",
"tokenization.storedPaymentMethodId": "BKG9RB2SBSHHSXT5",
"avsResult": "4 AVS not supported for this card type",
"avsResultRaw": "4",
"cvcResult": "1 Matches",
"cvcResultRaw": "M",
...
},
...
}
We are working to add more full-featured processor-specific examples. Please refer to Proxy examples for more request samples.
Don't hesitate to contact us if you need assistance with performing card transactions against a specific processor.
Save a Card
Once a card has been processed for the first time, merchants can store details in the long-term for future use and enable express checkouts, repeat transactions for subscription services, recurring payments and consumption-based charges. Merchants are responsible for obtaining explicit customer consent before saving card details, ensuring compliance with data protection regulations and fostering trust.
To do that, we can convert the Token Intent into a Token, by calling the Create Token API and passing the token_intent_id.
curl "https://api.basistheory.com/tokens" \
-H "BT-API-KEY: <PRIVATE_API_KEY>" \
-H "Content-Type: application/json" \
-X "POST" \
-d '{
"token_intent_id": "d2cbc1b4-5c3a-45a3-9ee2-392a1c475ab4"
}'
This operation returns a new or existing persistent Token depending on your fingerprinting and deduplication options:
{
"id": "1cd9c8bf-99fd-4784-ba69-68b15b301019",
"tenant_id": "74eca6ab-f94d-49bc-9f3c-6144eb3415ac",
"type": "card",
"card": {
"bin": "42424242",
"brand": "visa",
"last4": "4242",
"expiration_month": 12,
"expiration_year": 2025,
"funding": "credit",
"authentication": "sca_required"
},
"fingerprint": "BKJYqf2tcvhTHSXN7EvBJLviN3PBYRgwoJgce8VAfnSr",
"_extras": {
"deduplicated": false
},
...
}
What you should store in your database:
- [Required] - The token
id, associating it with the rightful customer account. - [Recommended] - The Network Transaction identifier returned by the processor during the initial transaction;
- This allows you to seamlessly charge the card with new processors or acquirers in the future and achieve the best approval rates.
- Refer to your current processor’s documentation or support for guidance on accessing this value.
- The card details (
brand,last4,expiration_month, andexpiration_year) if you plan to use it for things like rendering a stored card to your customer.- Alternatively, you can later retrieve the token to get that information from the API.
- The Processor Token if you plan to directly charge that card with the Processor (without going through Basis Theory Proxy).